

ABB participated as a Platinum Sponsor at the online ARC Industry Forum Asia titled Accelerating Industrial Digital Transformation and Sustainability on July 12-14, 2022. This Forum saw registrations of 1,600+ delegates for the two language tracks – Japanese and English. In the session on Industrial Cybersecurity, Ikshvakoo Vaid, Global Sales Leader – OT Security, ABB Energy Industries, spoke about the harsh realities of cyber risk to critical infrastructure that can be catastrophic from the environmental and safety perspectives. Although cyberattacks continue to occur, organizations are still reluctant to approach cybersecurity as a business priority. There has to be a shift in mindset and behavior and everyone working in the organization should be collectively responsible as guardians of cybersecurity.
At the end of this informative session, he joined the other speakers for the panel discussion. This blog highlights the salient points of Mr. Vaid’s presentation and his views at the panel discussion. The entire session can be viewed on YouTube.
There is a rising demand for cybersecurity skills in industry, explained Mr. Vaid. The global shortage amounts to about 2.7 million and 50 percent of this shortage is in the APAC region. Recruitment is challenging and adding qualified resources from academic institutions is not going to happen overnight. Hence it would be prudent to invest in existing resources, build robust processes, and implement carefully selected technologies so that cybersecurity underpins the business. However, when it comes to OT environments, cybersecurity is perceived to be complex, resource intensive, and expensive; as a result, there is often no overarching OT cybersecurity strategy. The security controls are siloed with no comprehensive view of the risks. It takes a lot of time and expertise to understand, maintain, and sustain these disconnected solutions.
Industrial environments prioritize production. Keeping old systems available with a tight regime of applications and maintenance of security controls that require some degree of human intervention to manage operational disruptions. Therefore, the OT teams running day-to-day operations find cyber security related tasks daunting and complex to handle. To put this in perspective, Mr. Vaid showed the journey and the different stages across a risk reduction roadmap:
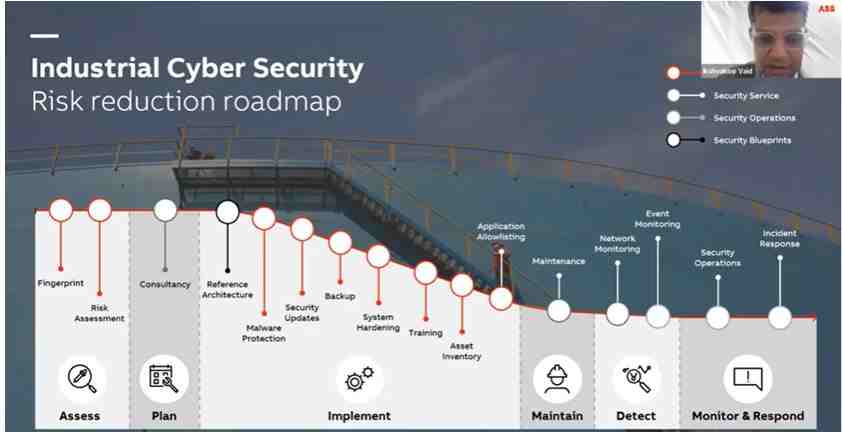
The time to traverse across this path from the extreme left to the extreme right depends on various factors, such as the current organizational maturity, the age, and the lifecycle of the current OT environments, etc. Mr. Vaid added that plants are juggling with different priorities, such as how much and on what to invest, identifying the right set of solutions for their operating schedules and so on. Despite the challenges, incremental progress is being made and as security controls and procedures are added, it results in multiple interfaces to monitor and maintain.
The Challenges
Security controls are only as effective as the teams maintaining them. The lack of actionable data and expertise lead to missed threats and improperly maintained security controls. According to a recent cybersecurity report, 48 percent of organizations were not even aware of the threats to their industrial control systems – and this is a matter of serious concern.
Mr. Vaid stressed that this is where a behavioral shift must be made and cyber risk must be discussed at the board level. It is hard to compute the ROI on the investment in security controls as it does not directly impact revenues and production. The broader question is “What is the cost of not investing in cybersecurity?” The dimensions of that response encompass issues related to production, safety, environment, social impact, and reputation to retain and attract investments. A well implemented cybersecurity strategy can reduce insurance premiums and partly or fully fund cyber efforts. Leaders must understand and support OT cybersecurity efforts and instigate an organizational cultural shift to prioritize trainings and action. Without a cultural or behavioural change, it is quite unlikely that any investment in technology could lead to long-term protection. Security executives must discuss the talent shortage and risks with the C-level executives and drive initiatives for the organic growth of inhouse security staff and skills through training programs. Everyone from plant managers to maintenance engineers should be cognizant of the threats and be empowered to implement and maintain security across critical assets.
A well thought out strategy implemented throughout the organization should be coupled with security tools designed for the people who work in the organization. Each team member should be motivated to be guardians of cybersecurity and keep operations on track. The benefits of partnering with a trusted solution provider with deep domain expertise are multi-fold as they can ensure that personnel are aware of the impending threats, implement solutions, and augment cyber workforce capacity and competence while companies scale up. Traditionally, cybersecurity solutions were expensive as they had to be deployed by experts. But the scenario has changed - technology that focuses on end users has the potential to shift their behaviors by empowering them.
Below are Mr. Vaid’s views during the panel discussion.
How do you drive that sense of ownership when it comes to OT cybersecurity?
Cybersecurity should be everyone’s responsibility – the key message here was to instill secure behavior which leads to organizational security. However, this does not necessarily mean that every engineer starts working on the cybersecurity procedures/tools. Rather, there must be a single point of contact. Someone who is accountable and demonstrates the way. Maintenance staff pick up these tasks and get trained on the job with support from the technology providers.
Is it necessary to have a certain percentage of certified cybersecurity personnel in the organization?
Certification is a great way to understand the subject and delve deeper into the topic. However, there are other areas such as regulatory frameworks, insurance etc. that require some extent of inhouse expertise. Certification definitely is a value-add when it comes to assessing risk profiles and there are diverse certifications available based on specific industrial applications.
Can “shifting behavior” be empirically measured?
It is difficult to understand and measure the change in behavior unless there are some metrics. We have noticed that organizations are having more conversations with employees in terms of procedures and tool utilization leading to a better ground level understanding of policies and implementation. For example, a best practice of deploying patches every 28 days may not be followed because of the task complexity. This is where effective communication and support really helps.

